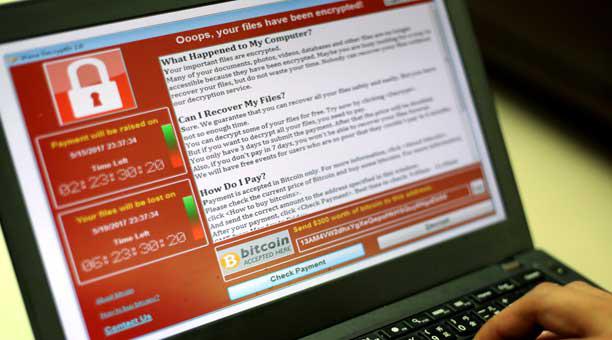
The WannaCry Effect. Beware of the Ransomware!
“Ooops, your files have been encrypted! Do not waste your time. Nobody can recover your data without our service”. Some hours after the warning message, 300 thousand devices in more than 150 countries collapsed due to one of the most powerful global cyber-attacks in recent years made by the WannaCry Ransomware.
Data abductions caused by this malware were spreading as fast as gunpowder, especially because of its strong ability to block the control of a computer by using asymmetric key encryption algorithms. In return, the user had to pay a sum of 300 to 600 dollars in Bitcoins. The economic impact was over $ 1 billion.
In these times when so many companies have a plan to protect their electronic assets, we end up believing that this is enough to avoid a cyber-attack. However, WannaCry proved that it is not enough to have a security plan. It is necessary to update every step that is taken in computer security.
Affected companies
Telefonica, the Spanish telecommunications giant, and the energy companies Iberdola, Gas Natural and Renault registered serious problems in their systems due to WannaCry. The UK’s National Health Service (NHS) was another major hit, particularly for abduction of something as sensitive as the health data of its patients.
CNPC, China’s state oil giant, also suffered the incidents of this major cyber-attack. While in Japan Hitachi and Nissan Motor, also saw their networks seriously damaged.
Why were these large corporations hacked despite having a planned design?
First, it was demonstrated that many of these organizations had their Windows out of date, WannaCry’s favorite system. The malware essentially took advantage of the variety of Windows versions existing in the world and the little update that is made of them.
It was also clear that in light of the great boom of technological solutions, business mobility and the practices of Bring your Own Device end business users of these devices don’t always properly benefit from the corporate defense systems.
Today there are lots of advanced threat detection solutions that can locate new malicious programs using sandboxing. But there are also countless modern malware that are aware of these sandboxing technologies and have incorporated methods to evade them.
WannaCry not only became so dangerous because it asked for a bailout to return the information, but also for its automatic way of operating. It is not a hacker replicating the malware, but a virus that spread itself and self-replicated, which was even more difficult to control. Once it was infiltrated, it was able to track the computers vulnerable to its infection.
Even though your company has not been a victimized by the WannaCry virus, alarms do not sound for nothing. Update not only your operating system, but also each of the computer security strategies that your organization is implementing.
If you wish to know which are the most widespread variants of Ransomware, 5 essential keys not to be scammed by malware and the most successful supplier companies in Ramsonware elimination, follow our next posts…
Don’t forget to visit our online shop where we have everything you need in terms of security!!
Remember that you can contact us 24 hours a day 7 days a week!